Rapid Incident Response & Ransomware Recovery
Minimize downtime. Protect your data. Restore your business—fast.
30+ Years of Cybersecurity & Manufacturing Experience
Led by a CISSP/CISM-certified expert with a proven track record in ransomware recovery and business continuity for New England manufacturers.
Local, Responsive, and Hands-On
We know your industry and region—no call centers, just direct access to senior consultants.
End-to-End Recovery
From attack containment to full system restoration and compliance documentation.
Why Choose 5 Star Data Systems?


What to Do If You’re Under Attack?
Disconnect Infected Devices
Immediately isolate affected systems to stop the spread.BUT DO NOT TURN THEM OFF!
Do Not Pay the Ransom
Paying does not guarantee recovery and may violate regulations. Often, the FBI will have tools to help.Contact Our Response Team
Please don't hesitate to contact us for help as soon as possible.

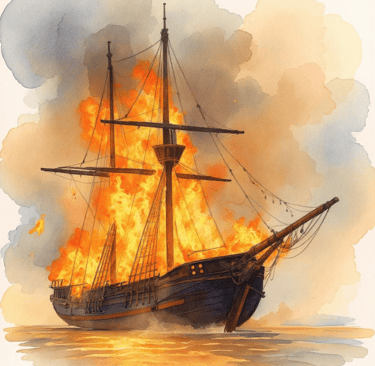
Incident Response & Ransomware Recovery Process
Production Shutdowns: Even a few hours of downtime can result in tens of thousands of dollars in lost revenue, missed orders, and a lost reputation.
Supply Chain Risk: One attack can disrupt your entire network of partners and clients.
Data Loss: Intellectual property, customer data, and operational recipes are prime targets.
Regulatory Fines: Non-compliance with CMMC or state laws can mean lost contracts and penalties


Why Ransomware Is Different for Manufacturers
5-Star Ransomware Prevention
Immutable, Off-site Backups: We implement and test 3-2-1-1-0 backup strategies to ensure you always have a clean recovery point.
Zero Trust Security Upgrades: Following a post-incident analysis, we can deploy advanced zero-trust controls to block future attacks.
Security Awareness Training: We train your team to spot phishing and social engineering, the #1 cause of ransomware breaches.
CMMC & NIST Compliance: Full documentation and support to keep your DoD contracts secure and active.


3-2-1-1-0: What is that?


The 3-2-1-1-0 backup strategy is a modern data protection framework designed to address evolving threats, such as ransomware, and ensure maximum data resiliency. Here’s what each number in the rule stands for:
3: Maintain at least three copies of your data. This includes the production (primary) data and at least two backup copies.
2: Store these copies on two different types of media (e.g., local disk and cloud, or disk and tape) to reduce the risk of simultaneous media failure.
1: Keep one copy off-site (physically remote or in the cloud) to protect against local disasters such as fire or theft.
1: Have one copy that is offline or air-gapped (completely isolated from the network) or stored on immutable storage. This protects against ransomware and cyberattacks that could compromise online backups.
0: Ensure zero errors in your backups by regularly testing and verifying backup integrity. This step guarantees that your backups are recoverable when needed.
How quickly can you respond?
It varied for New England clients, but usually within 1 to 3 business hours.
Should we pay the ransom?
Probably not. It is best to assess the situation and immediately contact the state police and the FBI. They can often have an application or a decryption key they obtained from previous investigations.
Can you recover encrypted data?
In many cases, yes—especially when best-practice backups are in place. We’ll assess and advise on all options.
Will you help with insurance and compliance reporting?
Yes, we provide all documentation needed for cyber insurance claims and regulatory audits.
Are results guaranteed?
No, unfortunately. This is why we need to implement prevention methods before it happens, thereby vastly reducing the risk of data loss.



Cybersecurity solutions for small and medium-sized manufacturers and businesses in New Hampshire and New England.
Contact Info
For Information
info@5sds.com
+1-603-338-6484
© 2025, 5 Star Data Systems LLC. All rights reserved.
We will not spam you. Promise.





